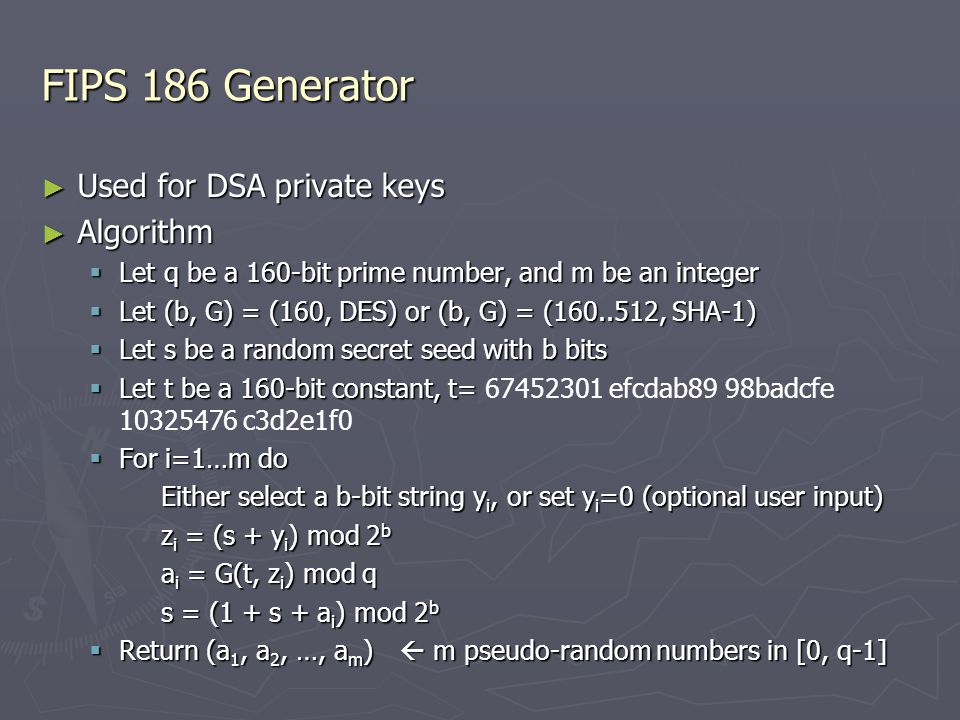
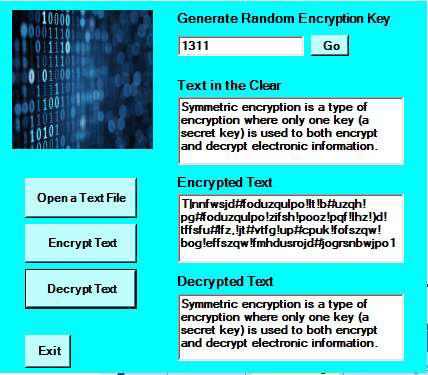
The secret key we generate is a random 30-character sequence from the... | Download Scientific Diagram

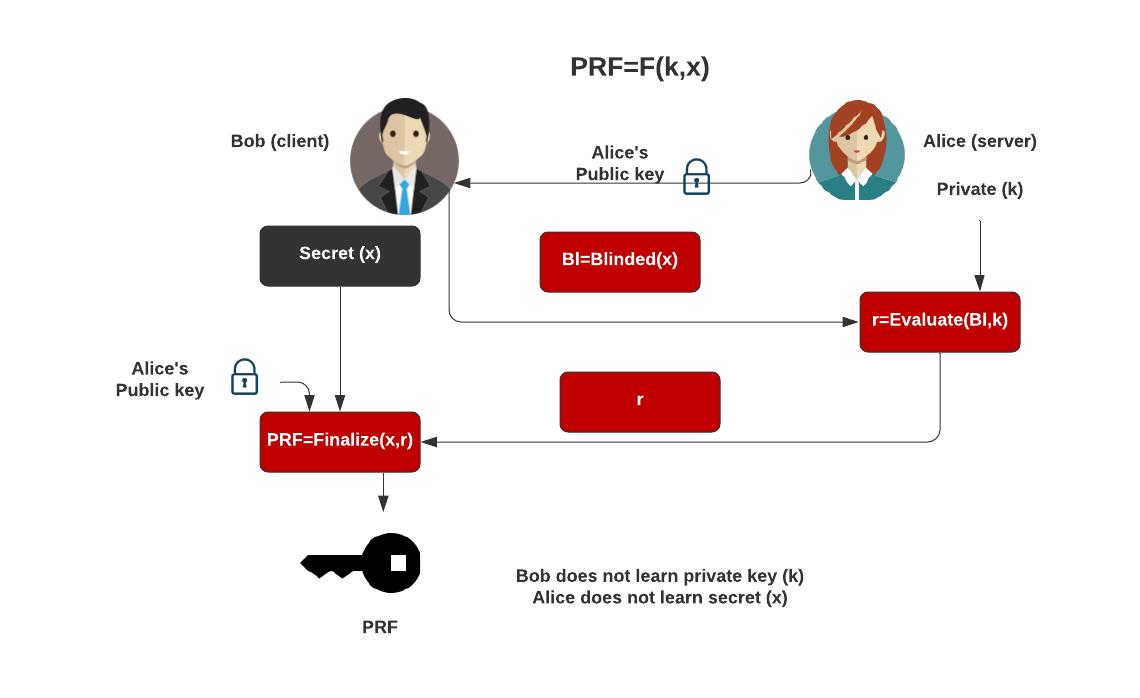
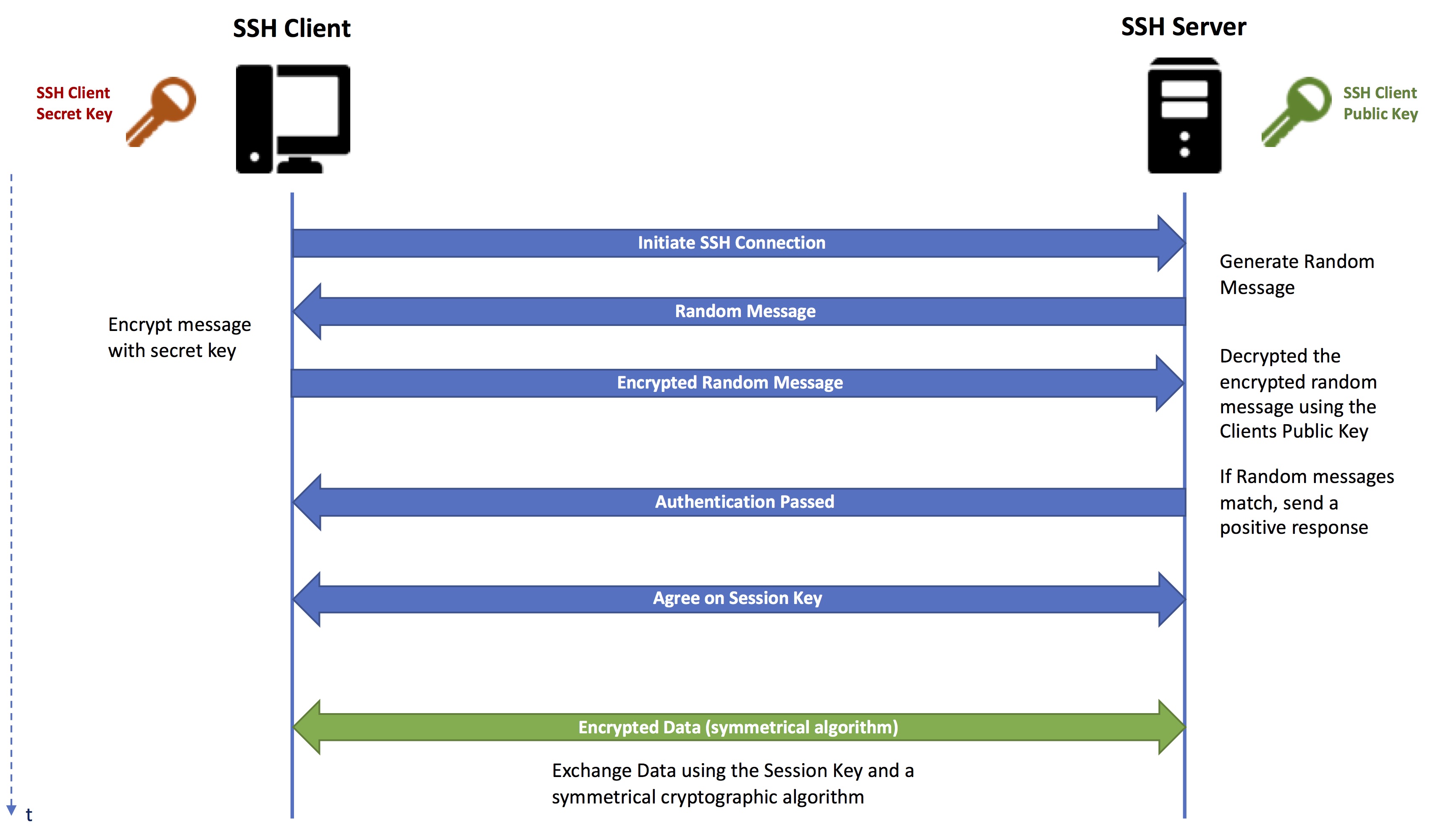
Block diagram of the proposed system. 3.1 Generation of The Seed The... | Download Scientific Diagram

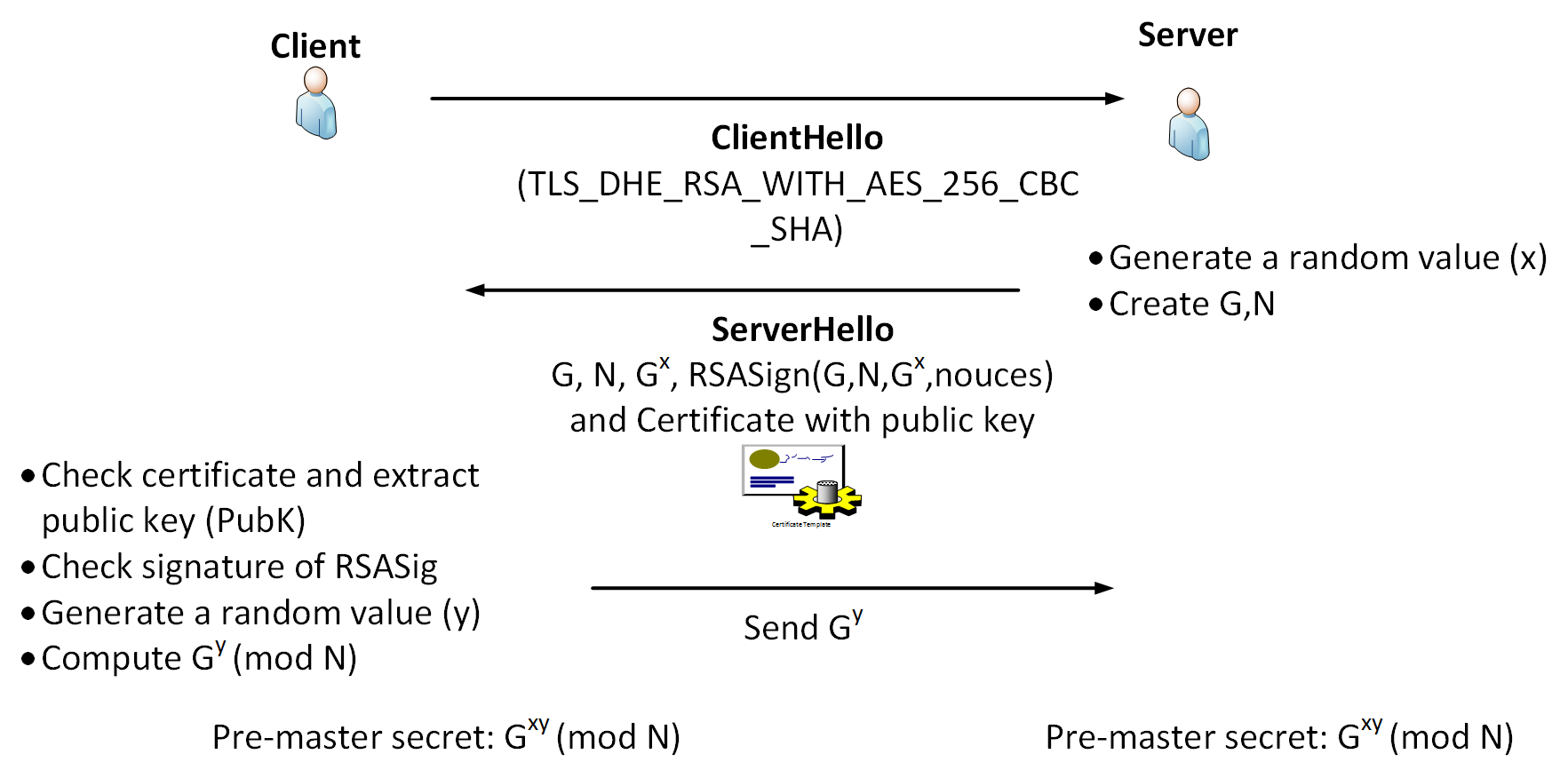
SOLVED: The Schnorr signature scheme is outlined below: Setup: g is a generator in group G with prime order q. Define a hash function H such that H:0,1* -> Zq. Key Generation:

The secret key we generate is a random 30-character sequence from the... | Download Scientific Diagram