Performing a vulnerability assessment on JBoss AS | Hands-On Web Penetration Testing with Metasploit

JexBoss - JBoss (and others Java Deserialization Vulnerabili... - vulnerability database | Vulners.com
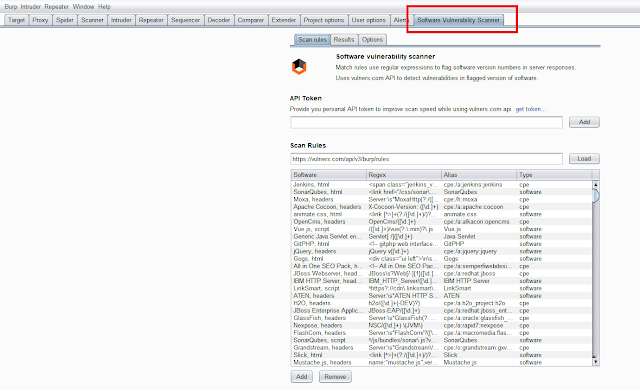
Unveiling the Power of the Software Vulnerability Scanner Extension in Burp Suite | by Career Technology Cyber Security India Pvt. Ltd. | Nov, 2023 | Medium
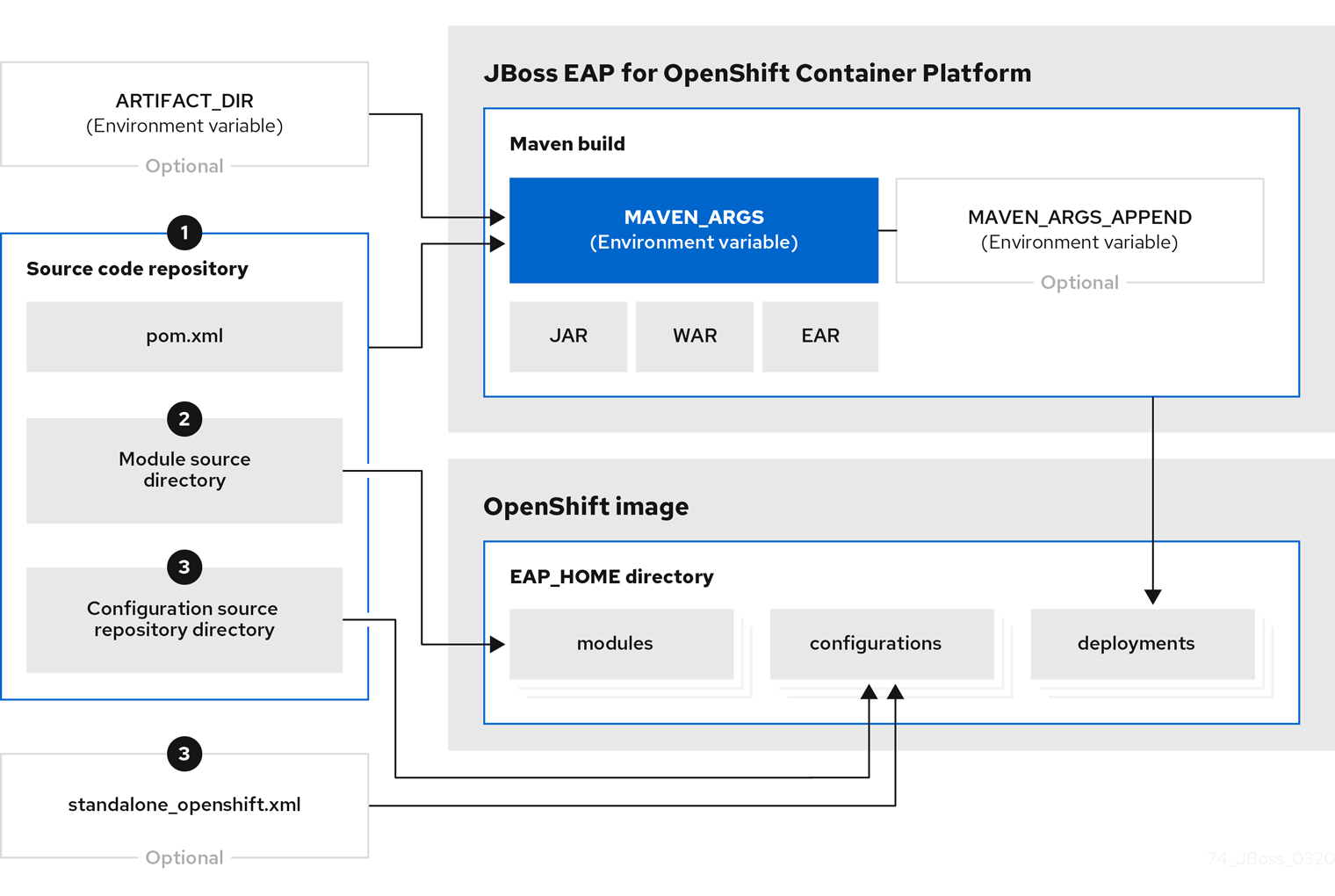
Getting Started with JBoss EAP for OpenShift Container Platform Red Hat JBoss Enterprise Application Platform 7.3 | Red Hat Customer Portal



![Security: Identifying Vulnerability in JBOSS [PCI Scan] Security: Identifying Vulnerability in JBOSS [PCI Scan]](https://i.ytimg.com/vi/I2Bfdaj91go/maxresdefault.jpg)