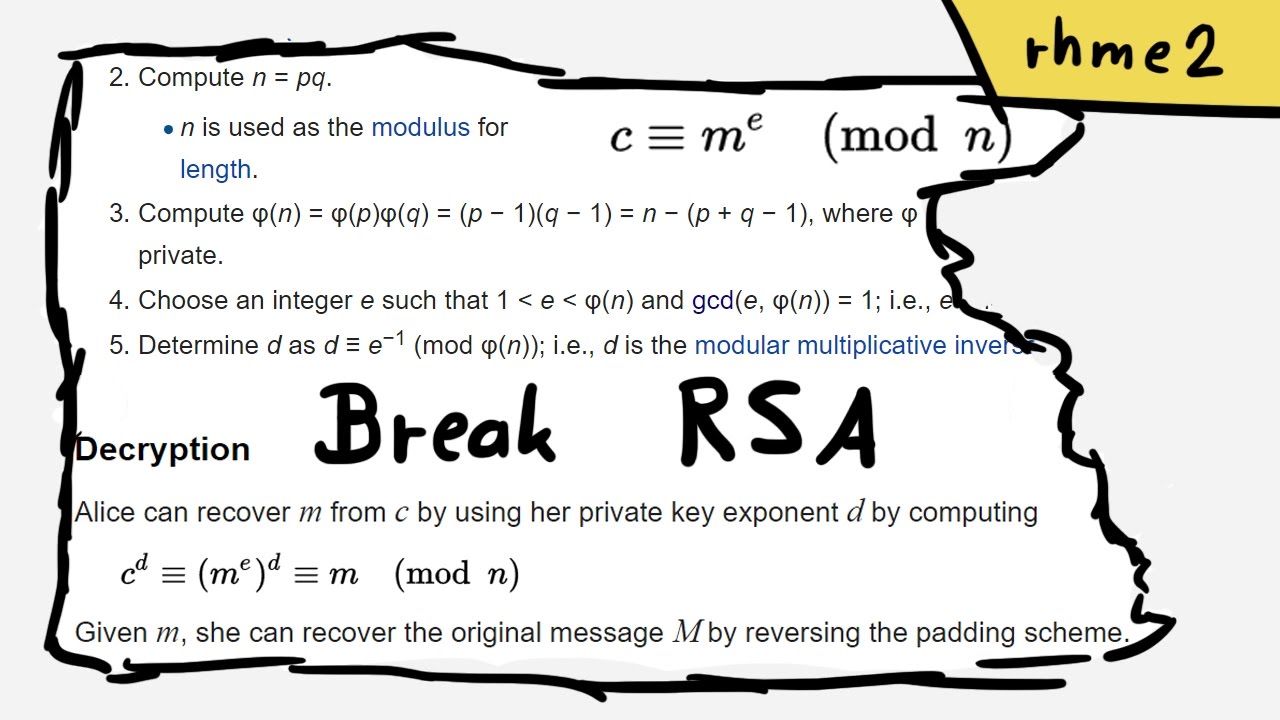
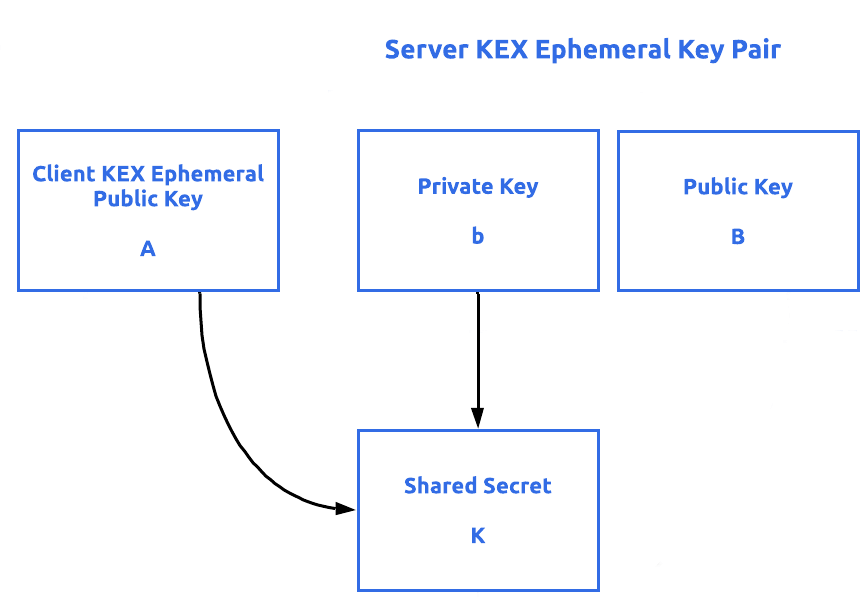
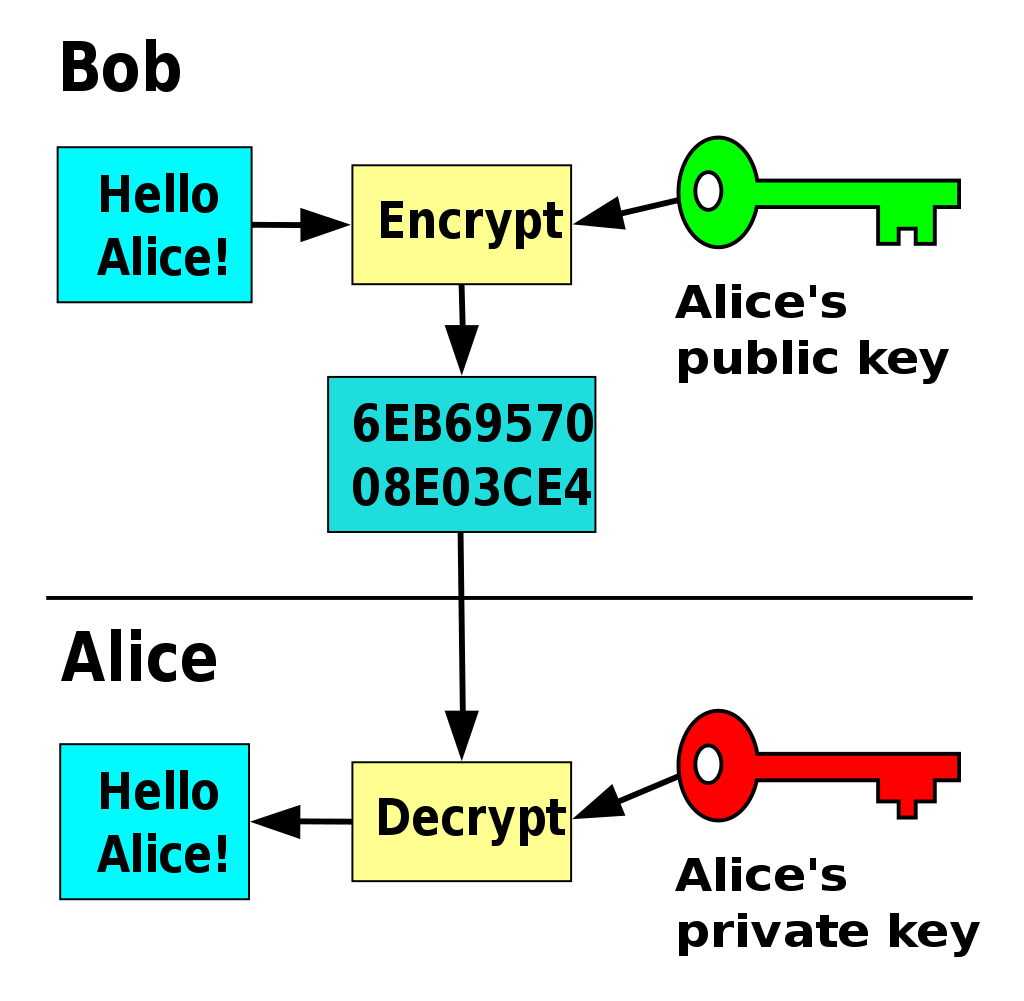
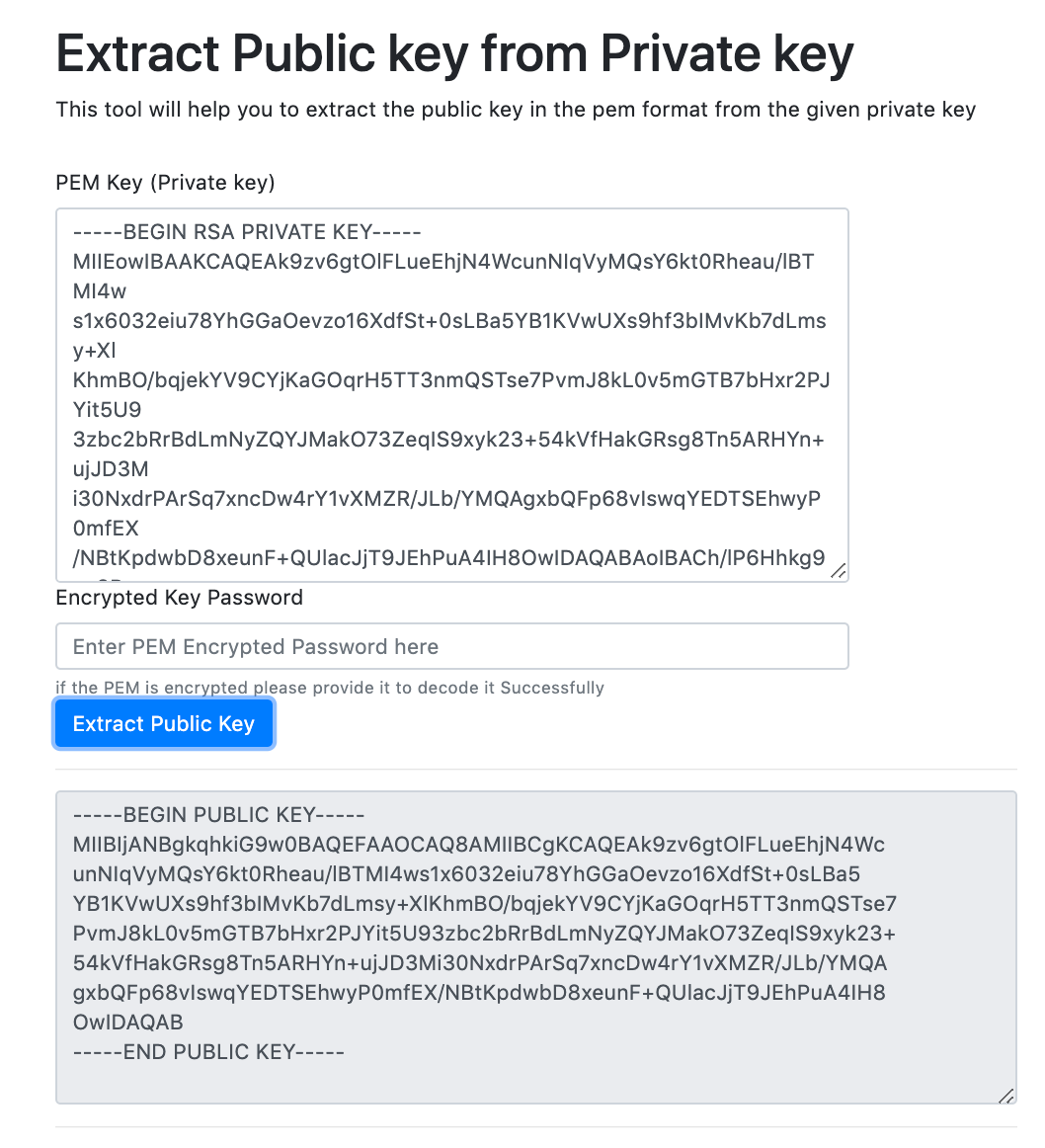
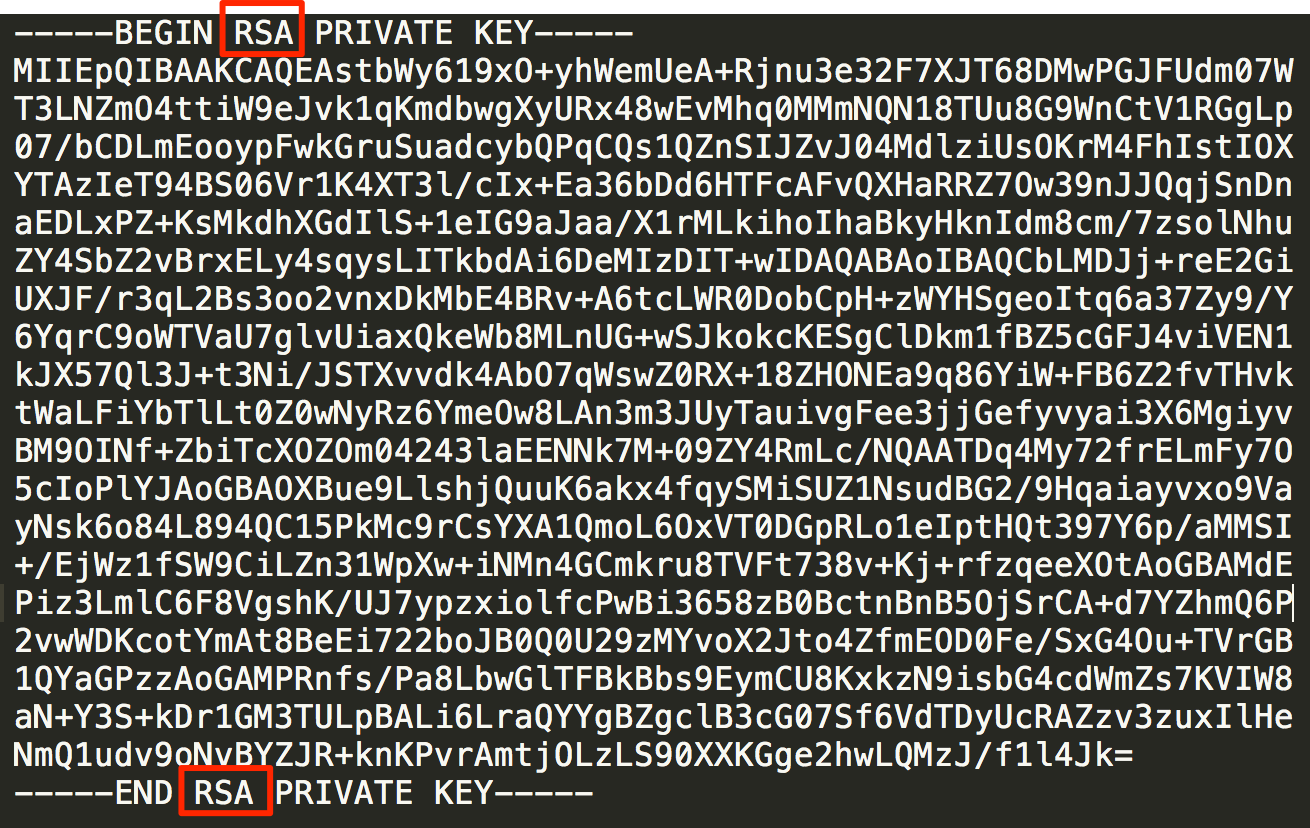
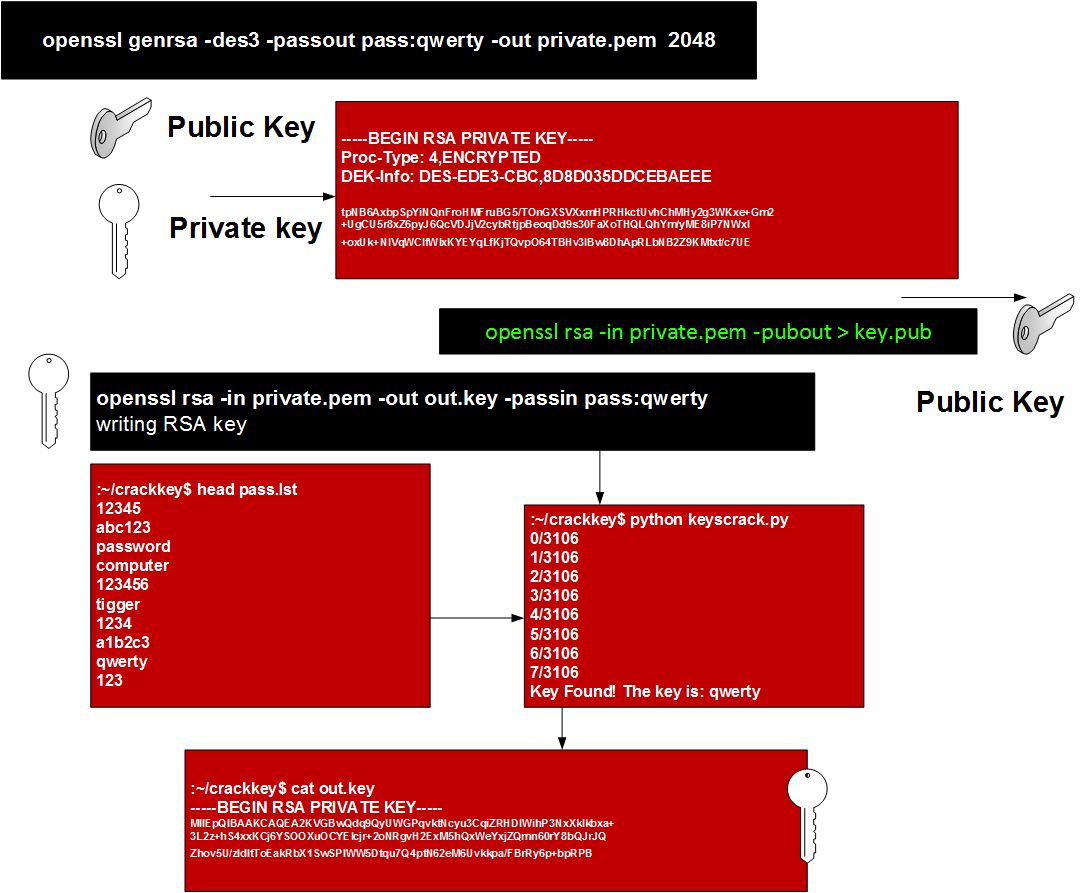
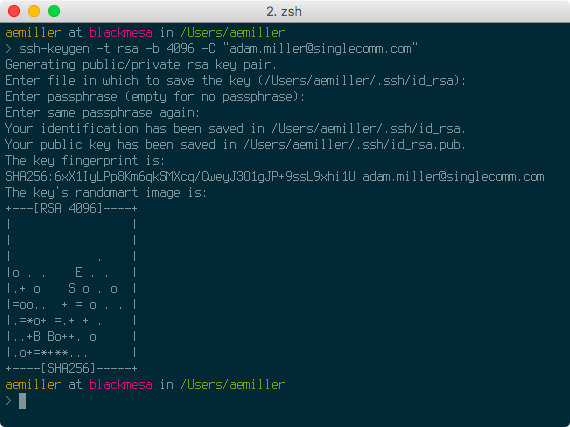
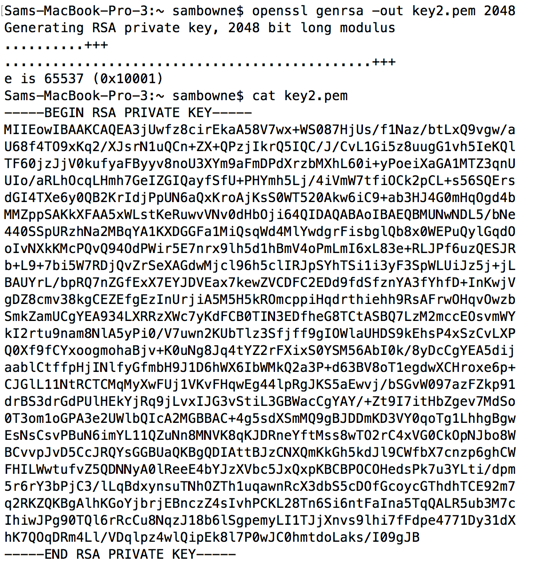
RSA Secret-Key Challenge: Cryptography, RSA Security, Encryption, Initialization Vector, Key, RC5, Distributed Computing, Brute Force Attack, Distributed.net - Surhone, Lambert M., Timpledon, Miriam T., Marseken, Susan F. | 9786130352806 | Amazon.com.au